Bad Memory - Forensics (MEDIUM) Huntress CTF Writeup
Bad Memory - Writeup
The task wants us to recover the password that the user has forgotten. I immediately thought of using Volatility 3 since we are working with an image or memory dump.
file image.bin
So straight to action, I decided to get the NTLM hashes from this image.
vol -f image.bin windows.hashdump
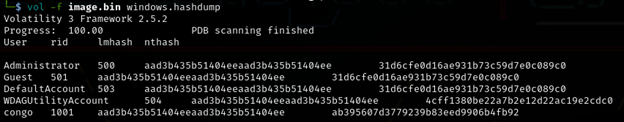
I saveed these hashes into a text file and fire up my favourite password cracker, John The Ripper to crack these hashes.
john --format=NT -w=/usr/share/wordlists/rockyou.txt hash.txt

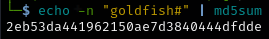
The only thing I have left is make the md5sum of this string to sumit as the flag format.
echo -n "goldfish#" | md5sum
flag{2eb53da441962150ae7d3840444dfdde}