BlackCat - Malware (EASY - not really) Huntress CTF Writeup
Black Cat - Writeup
In this challenge, I was given a zip file containing the malware.

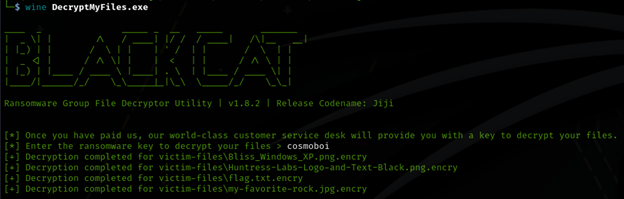
I could already see that the challenge was about decrypting the encrypted files inside the victim-files along with the NOTE.png that tells me what to do in order to get the files back.
I also saw the encrypted flag.txt along with some random files inside the “victim-files” folder.
Since this is a CTF challenge, I thought about investing this pictures as well using Aperi’Solve, a really good website to automate stenography.
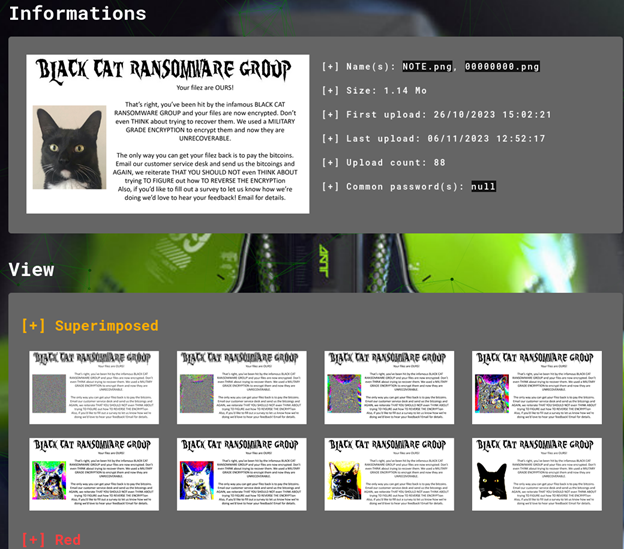
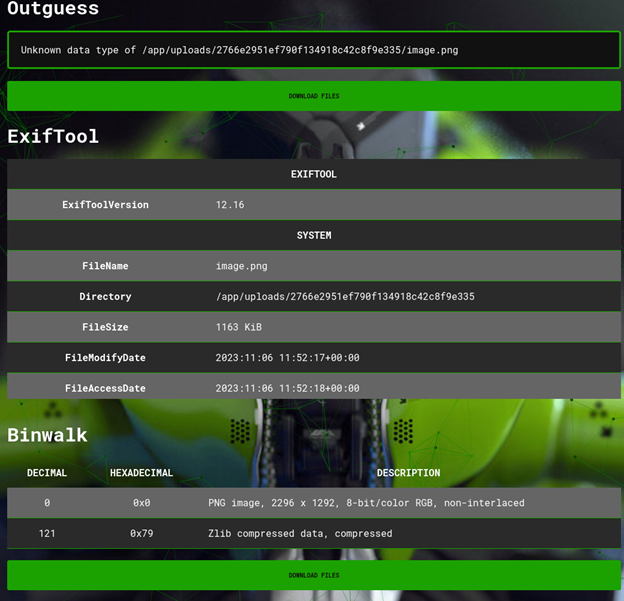
The picture seems pretty normal and nothing inside. Next, I opened the DecryptMyFiles.exe in Ghidra to inspect the file furthermore.
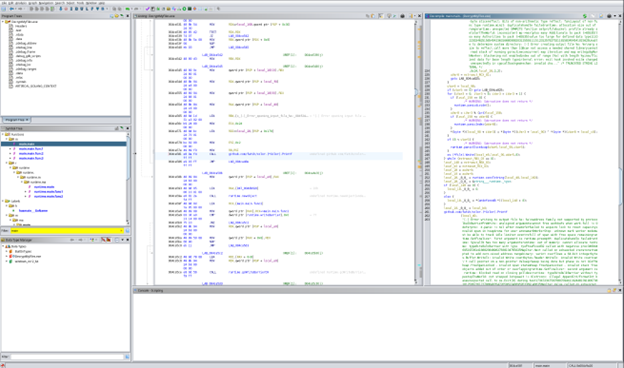
After inspecting the main function, I found out that the program was written in Go Lang, and also found the culprit and explanation to what kind of encryption the program is using. The program is accepting any key more than 8 characters.
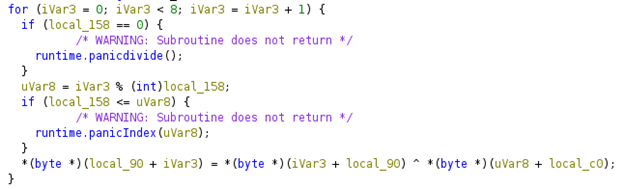
This is the part of the program where it is manipulating byte orders, a.k.a XOR’ing the files. The next step for me was to find a known original file and try to XOR the two files, to get the original decryption key.
Remembering that there was an encrypted file called “the-entire-text-of-hamlet.txt.encry”, I then decided to find the original text and compare both files.
https://gist.github.com/provpup/2fc41686eab7400b796b
I then saved the file into hamlet.txt, and then ran “diff” command to compare both files.
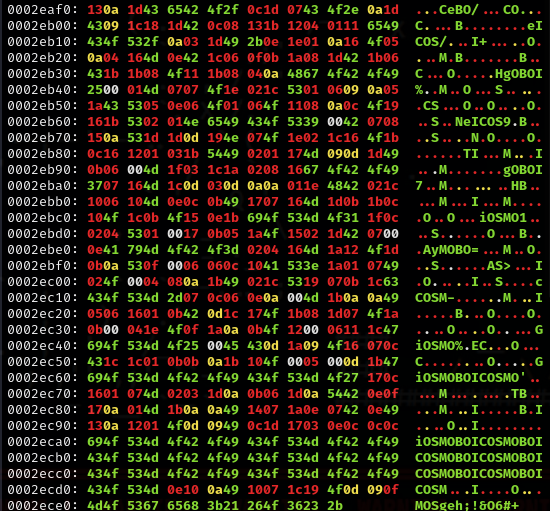
End of encrypted hamlet using xxd. xxd encryptedhamlet.txt
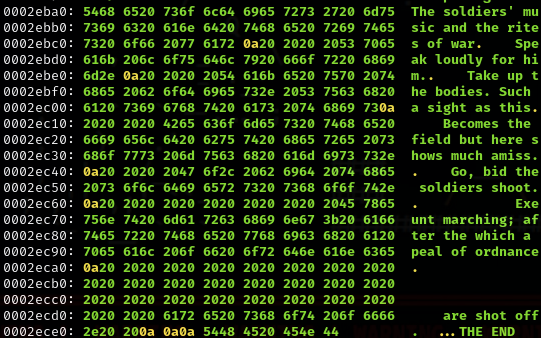
End of decrypted hamlet using xxd. xxd hamlet.txt
WAIT A SECOND
Hmm….. could it be that the decryption key is “COSMOBOI”? To be sure, I used this python script to XOR two files.
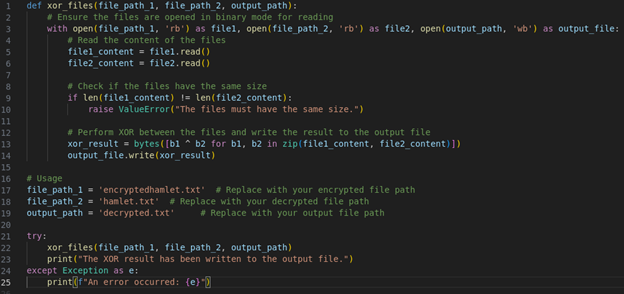
After running this script, I got to see that my susipicions were correct. The decryption key was “cosmoboi” which is 8 characters long.

I then decided to run wine for the decryption tool, and then put “cosmoboi” as the key, successfully helping me get the user’s files back!