Snake Eater - Malware (EASY) Huntress CTF Writeup
Snake Eater - Writeup
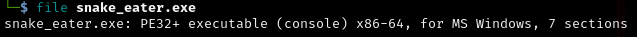
First things first, to analyze this malware, I had to examine what kind of file it was. Using file and strings command in Kali, gave me a view of what this file was doing.
file snake_eater.exe
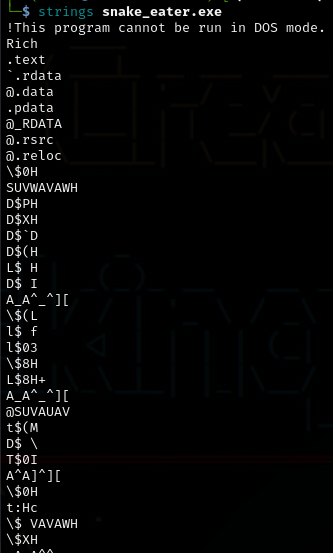
After analyzing the malware structure and description, I realied that the file was encrypted in some ways so I stopped and had to brainstorm a bit.
strings snake_eater.exe
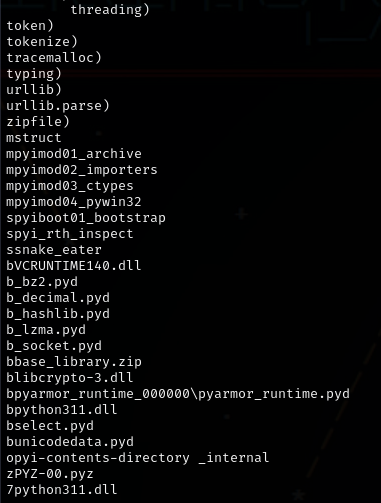
In order to get more information, I used the binwalk command in Kali to see more what it was doing.
binwalk -e snake_eater.exe
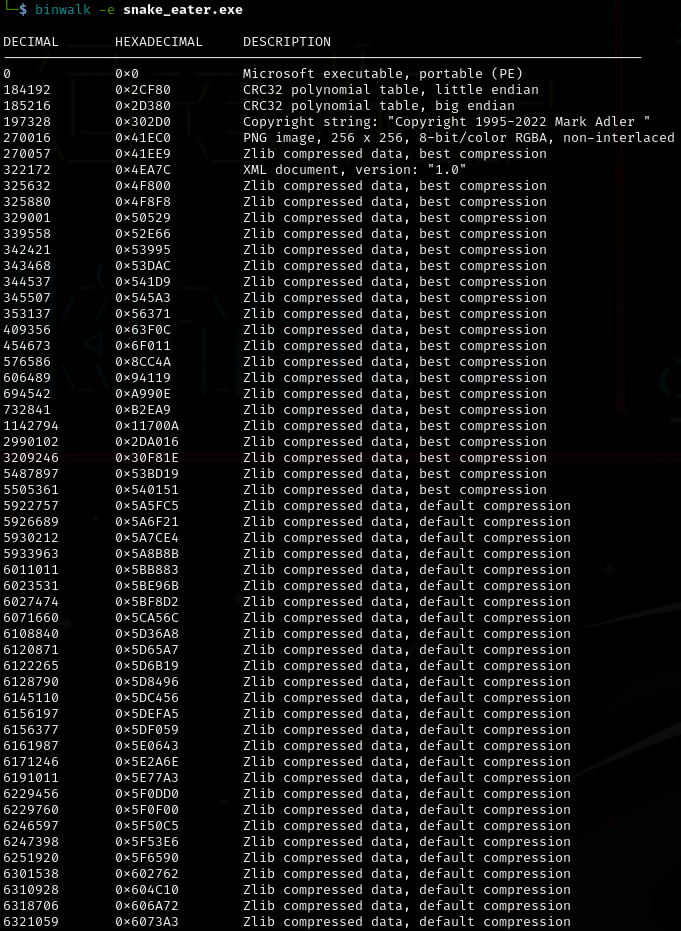
I found nothing useful because the data was encrypted.
Time to boot up Windows VM
Using windows, I saw this weird fie icon, just like the challenge description says.
Some google research later, I found that it was a python executable.
Back in Kali, I tried to decompile this file using this python executable script called PyInstaller Extractor v2.0.
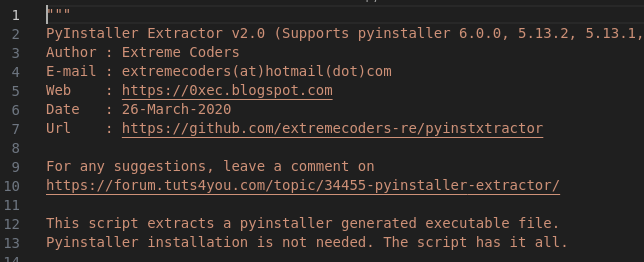
https://github.com/extremecoders-re/pyinstxtractor
After running the script, I got the extracted folders, and was able to see inside the structure of the malware.
extractor.py snake_eater.exe
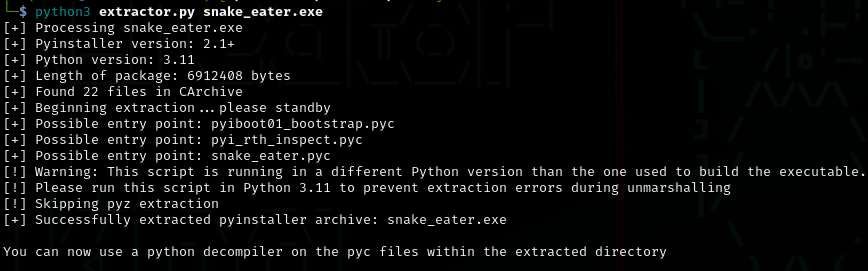
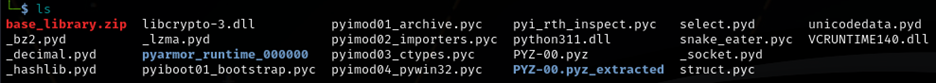
BAD NEWS:
I realized that the file was encrypted using pyarmor.
Running out of hope, I decided to run it dynamically in Windows using procmon.
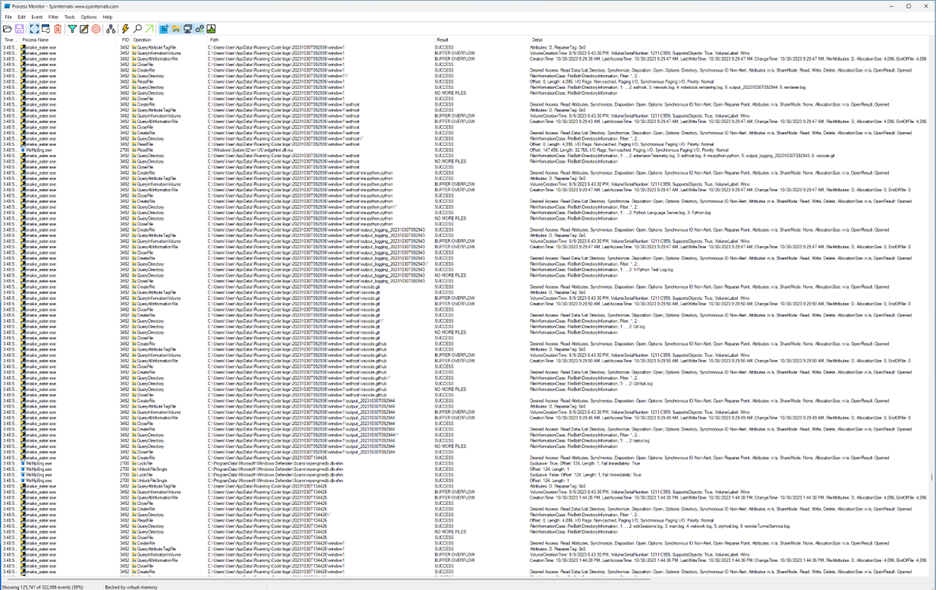
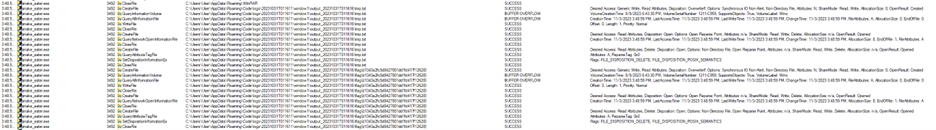
I could already see that the malware was doing A LOT. I wanted to see more so I had to filter the event logs using the filter option. Add this filter and apply.
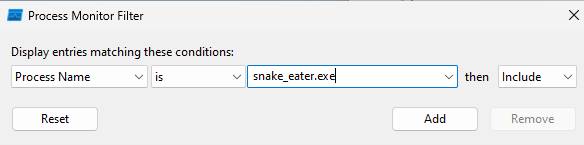
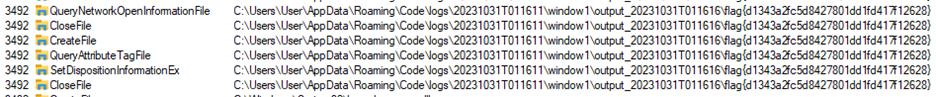
Just scrolling through the logs I was shocked because I could already see the flag in plaintext. :D